What is an API?
An API, or Application Programming Interface, allows different software applications to communicate with each other. It acts as a bridge, enabling data exchange and functionality sharing between programs without exposing the underlying code. APIs define a set of rules for how software components should interact, simplifying development and integration.
For example, when you use a weather app on your phone, it retrieves data from a weather service API. The app doesn’t need to store or process weather information; it simply makes an API call to request and display data from another system.
History of APIs
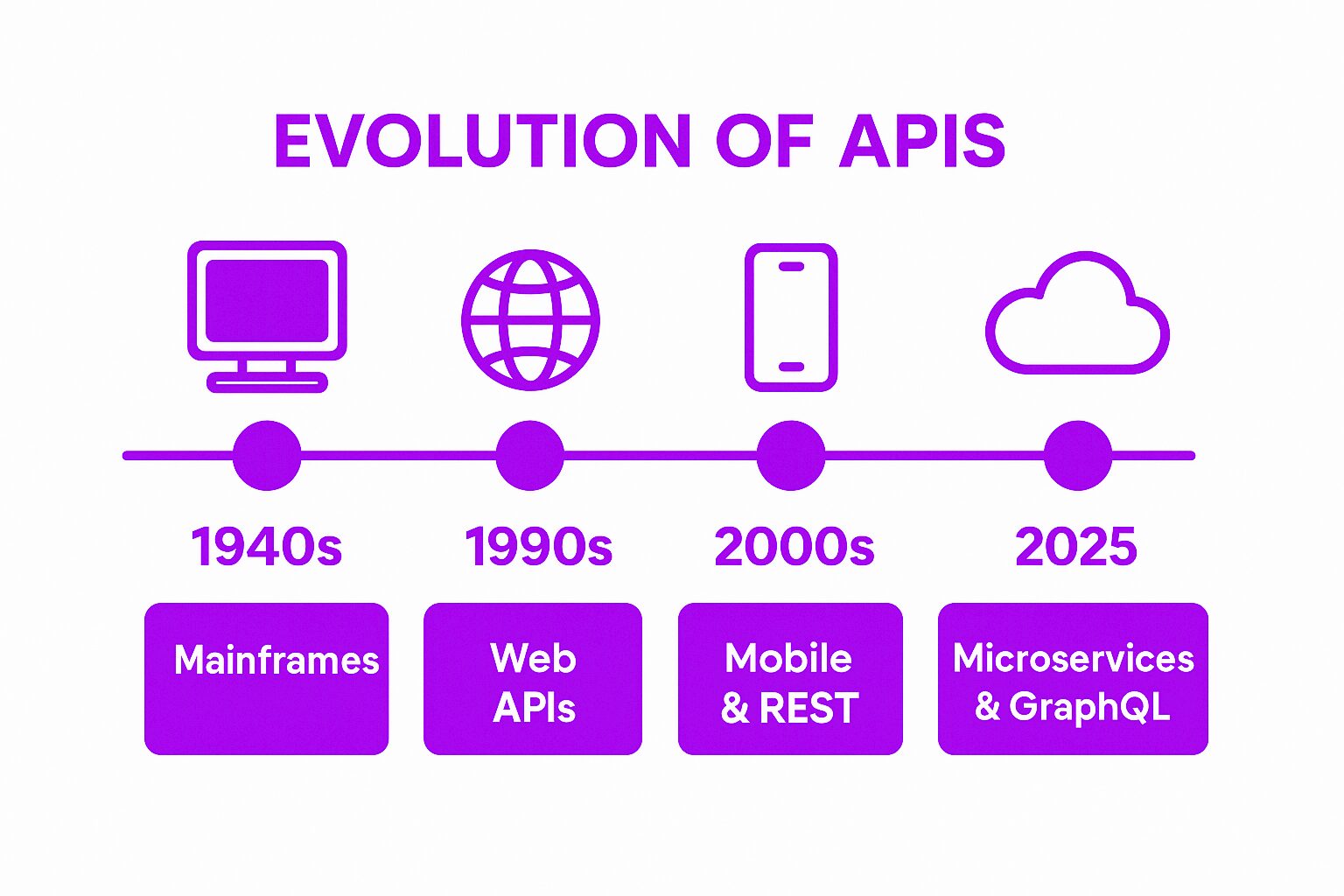
The concept of APIs has been around for decades, with the first APIs emerging in the 1940s. However, the term “API” did not gain widespread use until the 1960s and 1970s. During this time, APIs were primarily used for mainframe computers and were limited in their functionality.
Evolution of APIs
In the 1980s and 1990s, APIs began to evolve with the advent of the internet and the development of web technologies. This led to the creation of web APIs, which allowed different systems to communicate with each other over the internet. The introduction of Simple Object Access Protocol (SOAP) and Representational State Transfer (REST) further expanded the capabilities of APIs.
In the 2000s, the rise of mobile devices and cloud computing led to an increased demand for APIs. This resulted in the development of modern web APIs, which are designed to be developer-friendly and provide a wide range of functionality. Today, APIs are a crucial part of the digital landscape, with many industries relying on them to provide services and exchange data.
How APIs Work
APIs follow a request-response model. A client (such as an app or website) sends a request to an API endpoint, specifying what data or action it needs. The API processes the request and returns a response, usually in a structured format like JSON or XML.
A simple example:
-
A travel website wants to display flight prices from multiple airlines.
-
Instead of storing airline data, it uses airline APIs to fetch real-time prices.
-
When a user searches for a flight, the website sends requests to various airline APIs.
-
The APIs return pricing details, which the website presents to the user.
This process enables seamless data sharing without requiring direct access to a database or internal system.
APIs Work: Request and Response
APIs work by allowing different systems to communicate with each other through a request and response process. When a user interacts with an application, the application sends a request to the API, which then processes the request and returns a response. This response is then sent back to the application, which can then use the data to provide a service to the user.
For example, when a user searches for a product on an e-commerce website, the website sends a request to the API, which then retrieves the relevant data from a database. The API then returns the data to the website, which can then display the search results to the user.
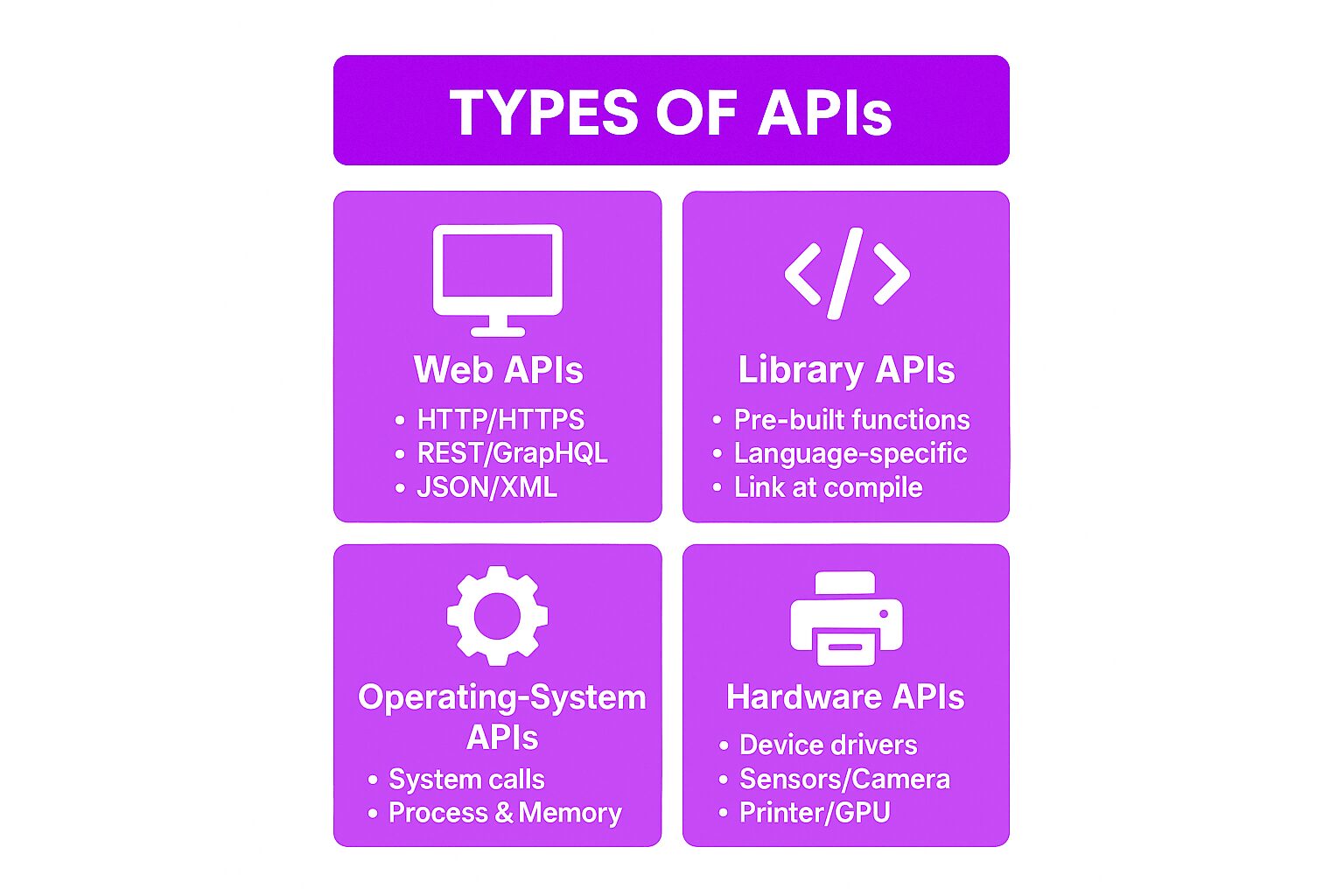
Types of APIs
APIs come in various forms, each designed for specific purposes. The main types include:
Web APIs
These APIs allow communication over the internet using standard protocols. The most common types are:
-
REST APIs: Follow REST (Representational State Transfer) principles and use standard HTTP methods like GET, POST, PUT, and DELETE.
-
SOAP APIs: Use XML-based messaging and are more rigid but offer better security.
-
GraphQL APIs: Allow clients to specify exactly what data they need, reducing unnecessary data transfer.
Library APIs
These APIs provide predefined functions that developers can use to build applications. For example, a graphics library API offers tools for rendering images. A notable example is the Java API, which provides a set of functions for building applications in the Java programming language.
Operating System APIs
These APIs allow applications to interact with the operating system. Examples include:
-
Windows API for accessing system features.
-
POSIX API for Unix-based systems.
Hardware APIs
These APIs enable software to interact with hardware components, such as printers, cameras, and sensors.
In some cases, hardware APIs may use remote procedure calls to interact with devices located on remote networks.
Internal vs. External APIs
-
Internal APIs: Used within an organization to connect internal systems.
-
External APIs: Made available to third parties, often for business partnerships.
Public and Private APIs
APIs can be classified into two main categories: public and private. Public APIs are available for anyone to use, while private APIs are restricted to specific users or organizations.
Public APIs are often used by companies to provide services to their customers. For example, a company may provide a public API for its customers to retrieve their account information or make payments. Private APIs, on the other hand, are often used by companies to provide services to their internal systems or partners.
Key Components of an API
Endpoints
An endpoint is a specific URL where an API can be accessed. For example, a weather API might have an endpoint like: https://api.weather.com/v1/current?location=NewYork
Methods
APIs use HTTP methods to define the type of operation:
-
GET: Retrieve data
-
POST: Send new data
-
PUT: Update existing data
-
DELETE: Remove data
Authentication
APIs use authentication to restrict access. Common methods include:
-
API Keys: Unique codes assigned to users or applications.
-
OAuth: A token-based authentication system.
-
JWT (JSON Web Tokens): Securely transmit data between parties.
Rate Limits and Throttling
APIs impose limits on the number of requests a client can make to prevent excessive usage and ensure fair access.
API Security
API security is a critical aspect of modern digital ecosystems. As APIs become more widespread, they also become a prime target for cyberattacks. Therefore, it is essential to implement robust security measures to protect APIs from unauthorized access and malicious activities.
API Security Strategies
There are several API security strategies that can be implemented to protect APIs from cyber threats. Some of these strategies include:
-
Authentication and Authorization: Implementing authentication and authorization mechanisms to ensure that only authorized users can access the API.
-
Encryption: Encrypting data transmitted between the API and the client to prevent interception and eavesdropping.
-
API Gateways: Using API gateways to manage API traffic and provide an additional layer of security.
-
Rate Limiting: Implementing rate limiting to prevent excessive API calls and prevent denial-of-service attacks.
-
API Documentation: Providing clear and concise API documentation to help developers understand how to use the API securely.
By implementing these API security strategies, organizations can protect their APIs from cyber threats and ensure the integrity of their digital ecosystems.
Why APIs Matter
APIs are fundamental to modern software development. They:
-
Enable applications to communicate without sharing internal code.
-
Allow businesses to integrate third-party services easily.
-
Reduce development time by leveraging existing functionality.
-
Support automation and workflow optimization.
-
Facilitate cloud computing and microservices architectures.
Benefits of APIs
Automation
APIs eliminate manual data entry by allowing systems to exchange information automatically. For instance, an HR system can use an API to update employee records across multiple platforms.
Scalability
Businesses can expand their services without overhauling existing systems. For example, an e-commerce platform can integrate new payment gateways via APIs instead of building its own payment system.
Security
APIs provide controlled access to data through authentication mechanisms. Instead of exposing entire databases, APIs allow specific data retrieval based on user permissions.
Interoperability
APIs enable different software applications to work together, regardless of their underlying technology stack. This is essential for cloud-based services and mobile applications.
Cost Savings
By using APIs, businesses can reduce development costs. Instead of creating new features from scratch, they can integrate existing services.
Challenges of APIs
Security Risks
Poorly secured APIs can expose sensitive data. Common threats include:
-
Injection Attacks: Malicious code inserted into API requests.
-
Data Leaks: Unintended exposure of user information.
-
Unauthorized Access: Weak authentication mechanisms exploited by attackers.
Versioning Issues
API updates can break existing integrations. To avoid disruptions, developers must manage versioning carefully and provide backward compatibility.
Dependency Risks
Organizations relying on third-party APIs are vulnerable to service outages or changes. If an API provider discontinues a service, dependent applications may stop functioning.
Performance Bottlenecks
Poorly optimized APIs can slow down applications. Factors affecting performance include network latency, inefficient queries, and excessive API calls.
Complexity
Managing multiple APIs across different systems can be challenging. API documentation, error handling, and compliance requirements add to the complexity.
Best Practices for API Usage
Choose the Right API Type
Select an API that aligns with your use case. REST APIs work well for most web applications, while GraphQL is better for optimizing data retrieval.
Implement Proper Authentication
Use secure authentication methods to protect your API. API keys, OAuth, and JWTs help prevent unauthorized access.
Monitor API Performance
Track API usage and response times using logging and analytics tools. This helps identify bottlenecks and improve reliability.
Ensure Backward Compatibility
When updating an API, maintain compatibility with older versions to avoid breaking existing integrations.
Rate Limit API Requests
Prevent abuse by setting request limits and throttling excessive traffic. This ensures fair usage and prevents server overload.
Maintain Clear Documentation
Well-documented APIs help developers understand how to use them. Include details on endpoints, request formats, authentication, and error codes.
Related API Concepts
Microservices & APIs
Microservices architectures rely on APIs to enable communication between small, independent services.
API Gateways
An API gateway manages API traffic, security, and analytics. It acts as a single entry point for multiple APIs.
Webhooks vs. APIs
Webhooks push data automatically when an event occurs, while APIs require requests to fetch data.
SDKs vs. APIs
Software Development Kits (SDKs) provide tools for building applications that use APIs, making integration easier.
Real-World API Use Cases
E-commerce
Online stores use APIs for payment processing (e.g., Stripe, PayPal), shipping tracking (e.g., FedEx, UPS), and inventory management.
Social Media
Platforms like Facebook, Twitter, and LinkedIn offer APIs for posting content, retrieving analytics, and integrating with other services.
Cloud Computing
Cloud providers such as AWS, Google Cloud, and Microsoft Azure use APIs for managing storage, computing power, and machine learning models.
Healthcare
APIs enable secure data exchange between hospitals, insurance providers, and healthcare apps, improving patient care and compliance.
Artificial Intelligence
AI-powered APIs provide features like natural language processing, image recognition, and predictive analytics.
Final Thoughts
APIs are essential for digital communication and modern application development. They enable automation, scalability, and security while reducing development time and costs. By following best practices, businesses can leverage APIs effectively while mitigating potential risks.